/
You never realize how many vulnerable BLE devices there are until you start sniffing.
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/24142246/Ubertooth_One.jpeg)
When you think about getting hacked, you mainly think of the basics: infrared, RFID, Wi-Fi, network security, door locks, etc. This is what people are usually worried about. But what about Bluetooth? What risks does it pose? And are there any tools in a DIY hacker’s arsenal to exploit it?
The answer is yes. Enter the Ubertooth One.
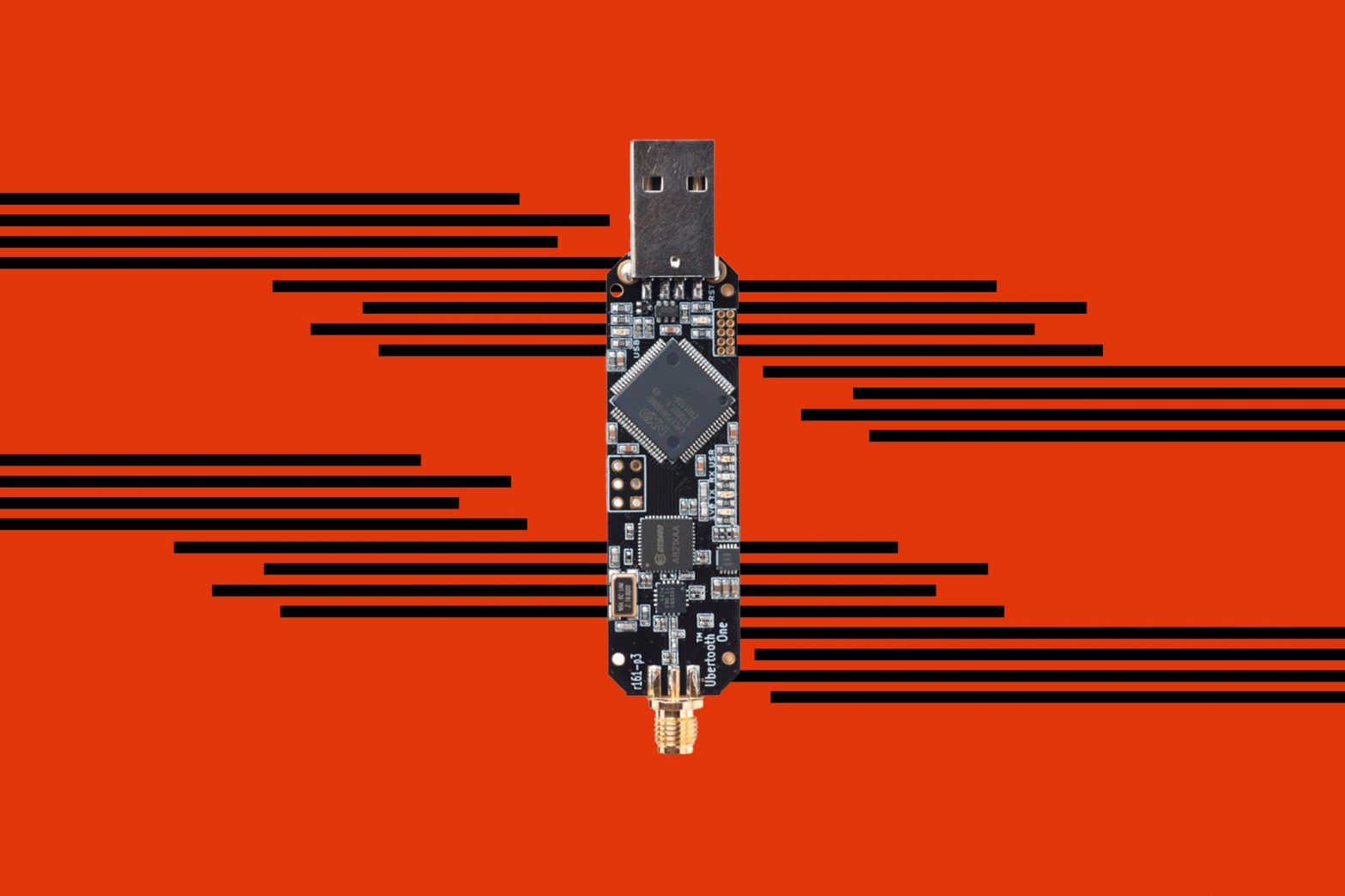
What is it?
The Ubertooth One is a small, open-source USB device with an antenna powered by an ARM Cortex-M3 chip and a CC2400 wireless transceiver. Plug it into your computer’s USB port, and you can sniff and monitor Bluetooth signals from nearby devices.
The Ubertooth itself is older technology, originally created by Michael Ossmann of Great Scott Gadgets back in 2011. There were Bluetooth monitoring devices before this, but they were mostly expensive and technical, like the Ellisys Bluetooth Explorer, which costs about as much as a used car. This version lets you do the same thing in a smaller, cheaper package — 125 bucks is a far, far easier pill to swallow!
What can it do?
The Ubertooth One was the first affordable Bluetooth sniffer, and it was a game-changer in a lot of ways. You can configure it to snoop on Bluetooth Low Energy devices using Wireshark, Kismet, and various other software (including at least one program used by the government). But it does have some severe limitations about what it can do. It is primarily for targeting the newer BLE standard, which is still useful because most of the innovations in Bluetooth in the last few years have revolved around BLE rather than the Bluetooth Classic standard. It is not, however, particularly good at sniffing Bluetooth Classic, and so that limits the range of what it can do for older devices.
How much of a threat is it?
While the Ubertooth One is not going to be as useful as a commercial Bluetooth sniffer, there is still quite a bit you can do with it or a similar device. There are tons of BLE devices out there, and many people don’t think about Bluetooth as a vulnerability.
That said, while the device is robust and has had a lot of support, there have been innovations within the space since it was created. Companies like Adafruit and Nordic Semiconductor also offer cheap dongles for sniffing BLE devices and various other attacks. You can even use the developer mode of an Android phone to snag Bluetooth logs, along with both Linux- and macOS-based computers. Programs like Wireshark and Bettercap allow you to extract quite a bit of information from Bluetooth devices. With a little bit of work, you can reverse engineer Bluetooth devices like heart rate monitors, blood pressure monitors, Bluetooth lockers, and much more. Or you could just reverse engineer a light, connect it to Home Assistant, and turn it on with a Python script.
Could I use it myself?
I won’t say you couldn’t. The project itself is mature, robust, and very well-documented for people that want to get out there and learn. Programs like Wireshark are actually fairly straightforward. But there are more intuitive devices than this one for a novice attempting to get into pentesting and hacking, and far easier places to start (like, say, the WiFi Nugget, for example, or even the Flipper Zero). And for a lot of people, an Android phone or a laptop with Kali Linux would get you pretty far.