A few years ago, a hacker managed to exploit vulnerabilities in Tesla’s servers to gain access and control over the automaker’s entire fleet.
In July 2017, Tesla CEO Elon Musk got on stage at the National Governors Association in Rhode Island and confirmed that a “fleet-wide hack” is one of Tesla’s biggest concerns as the automaker moves to autonomous vehicles.
He even presented a strange scenario that could happen in an autonomous future:
“In principle, if someone was able to say hack all the autonomous Teslas, they could say – I mean just as a prank – they could say ‘send them all to Rhode Island’ [laugh] – across the United States… and that would be the end of Tesla and there would be a lot of angry people in Rhode Island.”
What Musk knew that the public didn’t was that Tesla got a taste of that actually happening just a few months prior to his talk.
The Big Tesla Hack
Back in 2017, Jason Hughes was already well known in the Tesla community under his WK057 alias on the forums.
He was an early member of the Tesla “root access” community, a group of Tesla owners who would hack their own cars to get more control over them and even unlock unreleased features.
At the time, Hughes was using his knowledge to tinker with salvaged Tesla vehicles and build off-grid energy storage systems and electric conversion kits.
He turned the hobby into a business selling Tesla parts from salvaged vehicles and building his own controllers to help people make cool projects out of those parts.
At the time, he was also using his experience working with Tesla vehicles and Tesla software to report vulnerabilities in the automaker’s systems.
The practice, known as whitehat hacking, wasn’t his main focus, but like most tech companies, Tesla has a bug reporting system in place to reward people who find and report vulnerabilities.
He would occasionally submit bugs through that system.
After Tesla started to give customers access to more data about Supercharger stations, mainly the ability to see how many chargers were currently available at a specific charging station through its navigation app, Hughes decided to poke around and see if he could expose the data.
He told Electrek:
“I found a hole in the server-side of that mechanism that allowed me to basically get data for every Supercharger worldwide about once every few minutes.”
The hacker shared the data on the Tesla Motors Club forum, and the automaker seemingly wasn’t happy about it.
Someone who appeared to be working at Tesla posted anonymously about how they didn’t want the data out there.
Hughes responded that he would be happy to discuss it with them.
20 minutes later, he was on a conference call with the head of the Supercharger network and the head of software security at Tesla.
They kindly explained to him that they would prefer for him not to share the data, which was technically accessible through the vehicles. Hughes then agreed to stop scraping and sharing the Supercharger data.
After reporting his server exploit through Tesla’s bug reporting service, he received a $5,000 reward for exposing the vulnerability.
With now having more experience with Tesla’s servers and knowing that their network wasn’t the most secure, to say the least, he decided to go hunting for more bug bounties.
After some poking around, he managed to find a bunch of small vulnerabilities.
The hacker told Electrek:
“I realized a few of these things could be chained together, the official term is a bug chain, to gain more access to other things on their network. Eventually, I managed to access a sort of repository of server images on their network, one of which was ‘Mothership’.”
Mothership is the name of Tesla’s home server used to communicate with its customer fleet.
Any kind of remote commands or diagnostic information from the car to Tesla goes through “Mothership.”
After downloading and dissecting the data found in the repository, Hughes started using his car’s VPN connection to poke at Mothership. He eventually landed on a developer network connection.
That’s when he found a bug in Mothership itself that enabled him to authenticate as if it was coming from any car in Tesla’s fleet.
All he needed was a vehicle’s VIN number, and he had access to all of those through Tesla’s “tesladex” database thanks to his complete control of Mothership, and he could get information about any car in the fleet and even send commands to those cars.
At the time, I gave Hughes the VIN number of my own Tesla Model S, and he was able to give me its exact location and any other information about my own vehicle.
It’s at that point that Hughes decided to compile a bug report. Since he was already recently in contact with Tesla’s head of software security, who was Aaron Sigel at the time, he decided to email him directly with his finding.
This was a big deal.
Within minutes of receiving that email on that Friday afternoon in March of 2017, Sigel called Hughes.
Now back then, Tesla’s autonomous capabilities were much more limited than the driver-assist features found in Tesla’s Autopilot and Full Self-Driving packages now.
Therefore, Hughes couldn’t really send Tesla cars driving around everywhere like Tesla’s CEO described in a strange scenario few months later, but he could “Summon” them.
In 2016, Tesla released its Summon feature, which enables Tesla owners to remotely move their cars forward or backward a few dozen feet without anyone in them.
Until Tesla’s more recent “Smart Summon” update, it was primarily used to get cars in and out of tight spaces and garages.

While on the phone, Hughes then asked Sigel to give him the VIN number of the Tesla vehicle closest to him. The hacker proceeded to “summon” the car, which was in California, from his home in North Carolina.
At which point Hughes jokingly said that this bug report should be worth a brand new Tesla.
He didn’t end up getting a new Tesla, but the automaker awarded him a special $50,000 bug report reward — several times higher than the max official bug reward limit:
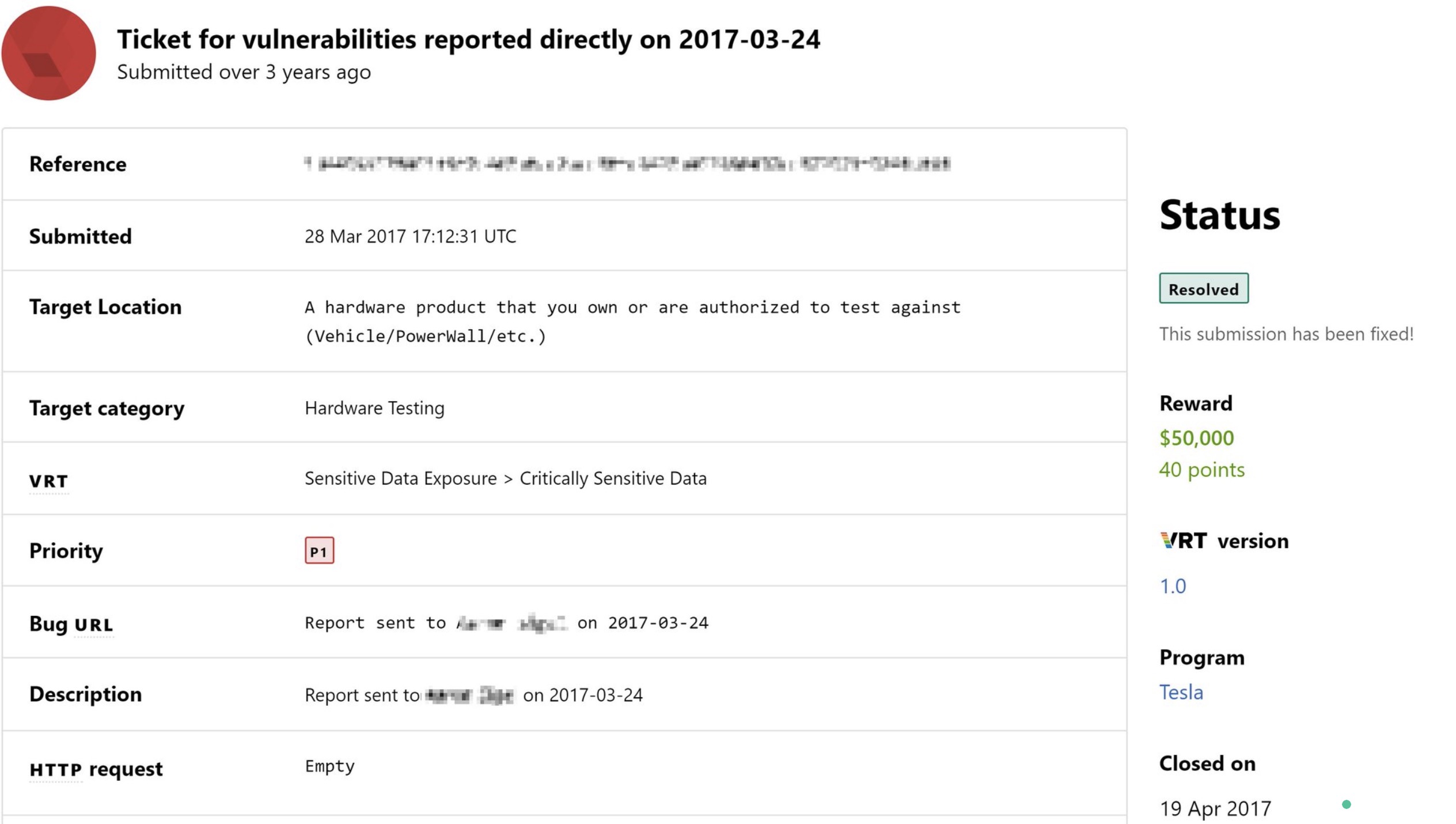
Tesla used the information provided by Hughes to secure its network.
That Friday, they ended up working overnight and managed to fix the main bug in Mothership within a few hours.
After a few days, they fixed the entire bug chain the hacker exploited to remotely gain control of Tesla’s entire fleet.
Tesla Cybersecurity Today
The good news is that Tesla has since significantly increased its effort to secure its network and overall cybersecurity.
The automaker increased its max payout per reported bug to $15,000 in 2018, and it has ramped up its security team as well as its relationship with hackers through participation in hacking conferences.
Over the last few years, Tesla has brought its cars as targets in the popular Pwn2Own hacking competition.
David Lau, vice president of vehicle software at Tesla, recently commented on the effort:
We develop our cars with the highest standards of safety in every respect, and our work with the security research community is invaluable to us. Since launching our bug bounty program in 2014 — the first to include a connected consumer vehicle — we have continuously increased our investments into partnerships with security researchers to ensure that all Tesla owners constantly benefit from the brightest minds in the community. We look forward to learning about, and rewarding, great work in Pwn2Own so that we can continue to improve our products and our approach to designing inherently secure systems.
Also, Tesla owners will supposedly soon get two-factor authentication for their Tesla account.
Electrek’s Take
While this was a massive breach exposing a big vulnerability in Tesla’s network, it is also a good example of the importance of whitehat hackers and for them to focus more on the automotive industry as cars become increasingly more connected.
Instances like this important breach are actually putting Tesla in a much better position in the industry.
The automaker’s products are sort of becoming the cool new thing for hackers to hack like the iPhone once was.
As long as the good guys, like Jason, are doing it, it will help Tesla stay ahead of the bad guys and avoid the possible nightmarish scenario of self-driving vehicle attacks described by Elon.
FTC: We use income earning auto affiliate links. More.

Subscribe to Electrek on YouTube for exclusive videos and subscribe to the podcast.