Dealers in the US were hit by cyber-crime last month with twin attacks on CDK Global. What can UK dealers learn from their experience?
Dealers in the US were hit by cyber-crime last month with twin attacks on CDK Global. What can UK dealers learn from their experience?
Software and dealer management systems giant CDK Global was hit by two cyber-attacks in the USA in June, forcing it to shut down its applications for US dealers. The company services 15,000 outlets across the US, with thousands of dealers and most OEMs on its books.
After the second hit, it shut down its systems, assessed the impact and provided updates to dealers on the state of play. A week later it reported that it had got a small test group of dealers live on its dealer management system (DMS). It said once it was sure that the system was working and secure it would being other dealers on board. CDK Global reportedly paid $25m to the hackers who forced it to close down its systems. CNN reported “multiple sources” revealing that the company had paid the ransom to allow it to get its systems up and running again. CBT reported that CDK Global CEO Brian MacDonald had sent a letter sent to over 15,000 dealerships, acknowledging the challenges posed by CDK’s cyber attacks. It said the letter did not disclose specific compensation plan details, but MacDonald indicated that CDK’s Customer Engagement Team would provide further information.
Cyber-crime has been on the rise over the past decade. In the UK, dealer groups, including Pendragon and Arnold Clark and JCT 600 have been targeted. And these are the reported cases, there are others that flew under the radar.

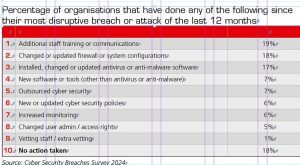
The government-published Cyber Security Breaches Survey 2024 published in April this year looked at cyber threat across the board, for all types of businesses. Over half (50%) report having experienced some form of cyber security breach or attack in the last 12 months. This is much higher for medium businesses (70%) and large businesses (74%).
By far the most common type of breach or attack is phishing (84% of businesses). This is followed, to a much lesser extent, by others impersonating organisations in emails or online (35% of businesses and then viruses or other malware (17% of businesses).
So, what can dealers do to help prevent damage due to cyber-attacks? Three specialists in the US had some useful practical advice to offer UK dealers.
Satnam Narang, senior staff research engineer at Tenable, said: “All organizations must understand they are a likely ransomware target.
“In order to protect themselves they must master the basics – cyber hygiene, cyber education and cyber response plans. While we don’t know now how CDK was compromised, most cyber-attacks exploit basic cyber mistakes.”
Pieter Arntz, malware analyst at Malwarebytes, said: “Dealer groups need readily deployable and clean backups or a rollback system.
“[They need] an emergency plan on how to act when systems go down, so you don’t lose customers due to being unable to respond. Preferably a plan that has been tested to see what works and what doesn’t.
“[They need] to thoroughly investigate and remediate how the attacker got in and what they left behind, so you don’t get attacked twice and to reset all staff passwords, because you have to assume they have been compromised.”
Andy Thompson, offensive cybersecurity research evangelist at CyberArk, said: “To ensure dealer groups remain safe and resilient against cybercrime, it is crucial to adopt a comprehensive approach to identity security.
“This applies universally across industries but is particularly pertinent for dealer groups due to their complex ecosystems of human, machine, and AI interactions.
Thompson put forward some key strategies to help dealers combat the threat of cybercrime using some well tried and tested techniques. They are by no means infallible, but they are a start for some small companies out there.
 Establish multiple layers of cybersecurity controls. Protect all identities—human, machine, and AI—with robust authentication measures, such as multi-factor authentication (MFA), to add an extra layer of security.
Establish multiple layers of cybersecurity controls. Protect all identities—human, machine, and AI—with robust authentication measures, such as multi-factor authentication (MFA), to add an extra layer of security.
Regular training and awareness programs for all employees are essential. Ensure that your team is well-versed in recognizing phishing attempts, social engineering tactics, and other common cyber threats.
Thoroughly assess the cybersecurity practices of your third-party vendors and supply chain partners. Ensure they adhere to stringent security standards and have contingency plans in place to mitigate any potential risks to your operations.
Conduct regular security audits and keep all systems and software up to date with the latest patches. This helps to close any vulnerabilities that could be exploited by cybercriminals.
Prepare for potential cyber incidents by developing and regularly testing incident response plans. These plans should outline clear procedures for detecting, responding to, and recovering from cyber attacks.“By focusing on these areas, CEOs of dealer groups can create a robust cybersecurity posture that minimizes the risk of falling victim to cybercrime. This multi-faceted approach ensures comprehensive protection and prepares organisations to respond effectively to any threats that may arise,” said Thompson.